Summary
Pre-requisite requirement: To proceed with the installation please make sure the following URL are trusted sites within internet explorer on the server where you have installed RealTime Service:
To set up RTS with modern authentication, we need an O365 service account and Azure Graph access.
O365 service account
We need a service account in O365 with the following conditions:
- Must have a mailbox.
- Cannot be hidden in GAL.
- Must be configured with “Application Impersonation Role” as described here:
https://docs.microsoft.com/en-us/exchange/client-developer/exchange-web-services/how-to-configure-impersonation (From Microsoft)
https://support.add-on.com/article/273-steps-to-configure-application-impersonation-rights-in-exchange-servers (Our KB with some explanations)
Azure Graph access
Resource Central needs a connection to AD in order to look up people, locate mailboxes and read basic information, and in O365 this information resides in Azure. In order to access Exchange Web Services with Modern Authentication we also need a delegated EWS access through Azure Graph. Access to this information requires the registration of an Azure Application, which can be created as described in the following:
1. Log on Azure portal with your Azure account.
2. If your account gives you access to more than one, click your account in the top right corner, and set your portal session to the desired Azure AD tenant.
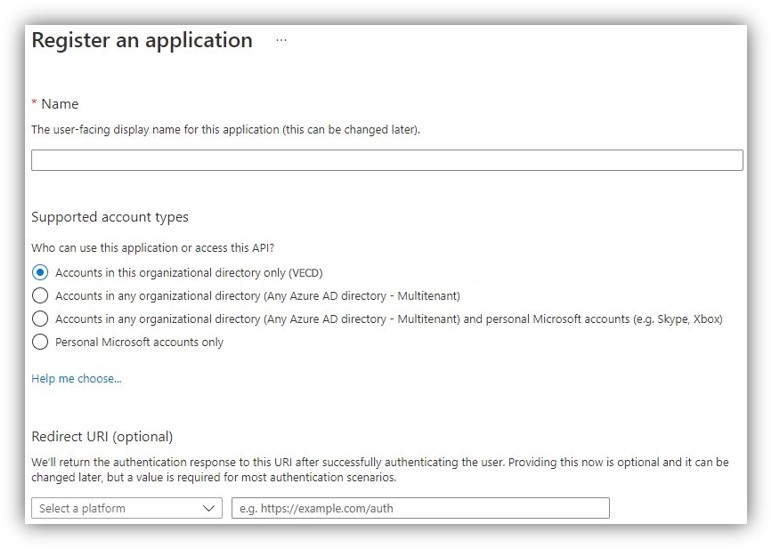
3. On the left-hand navigation pane, click the Azure Active Directory service (if it absent, click on All services and find it by name), click App registrations, and click New registration.
4. When the Register an application page appears, enter your application's registration information:
- Name: Enter realtimeservice (or any name you want).
Note: Name of the web app must not include spaces or digits. - Supported account types: Select ‘Accounts in this organizational directory only’.
5. When finished, click Register.
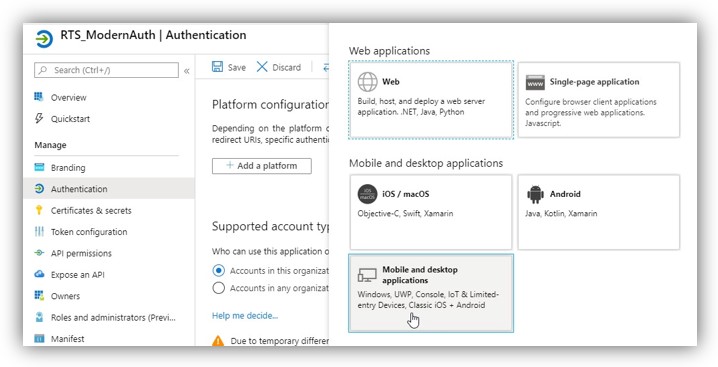
6. Go to Authentication > Add a platform
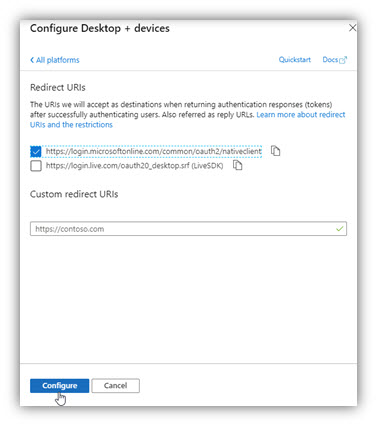
Select Mobile and desktop application and then select the OAuth2 redirect URI and click configure to complete Authentication configuration.
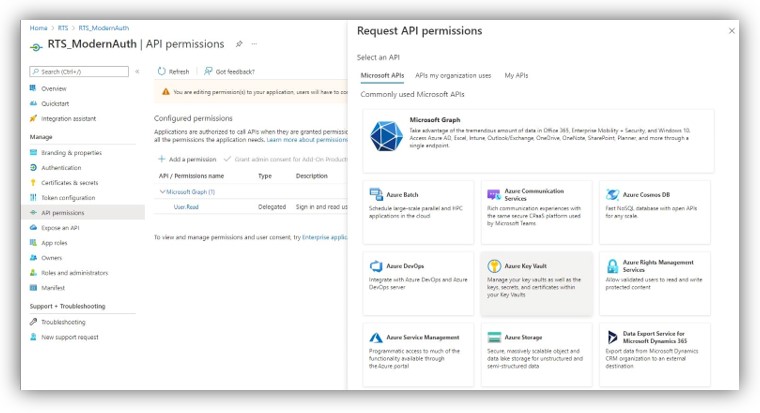
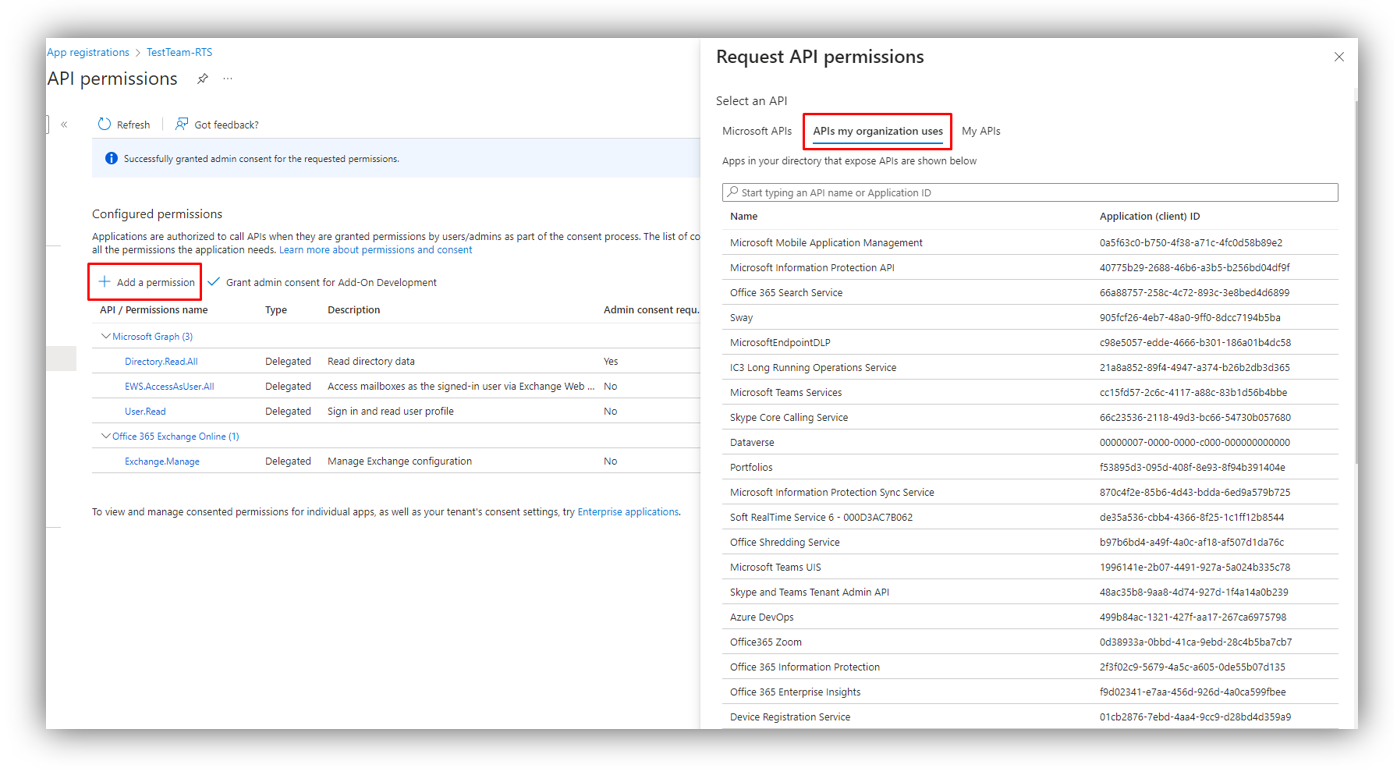
7. Next click the API Permissions section on the menu > Add a permission.
In the Request API permissions panel, you will need to work on Microsoft Graph section as shown in the following figure:
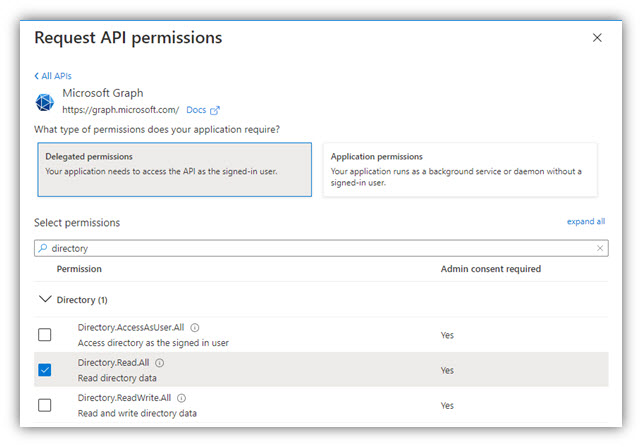
8. Enter Microsoft Graph and add the delegated permission Directory.Read.All
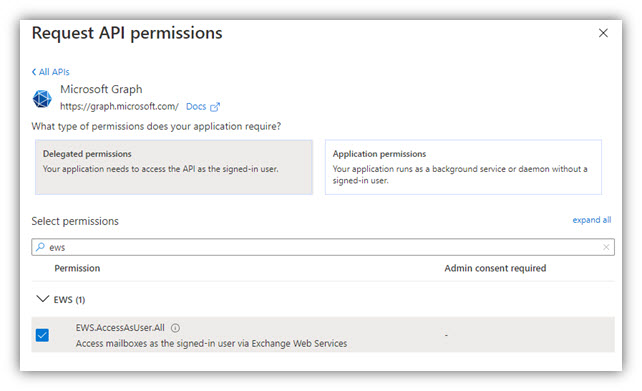
9. Also in Microsoft Graph, add the delegated permission EWS.AccessAsUser.All
Click on Add a permission to finish adding the permission.
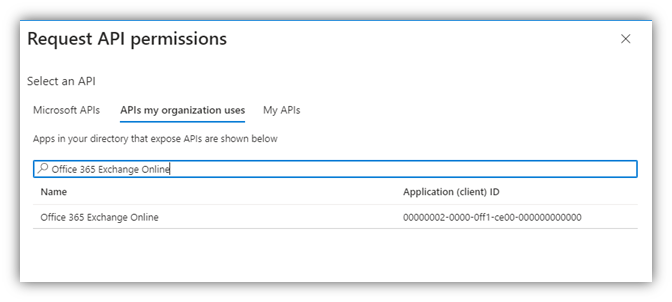
10. Go to APIs my organization users.
Then, search for Office 365 Exchange Online section.
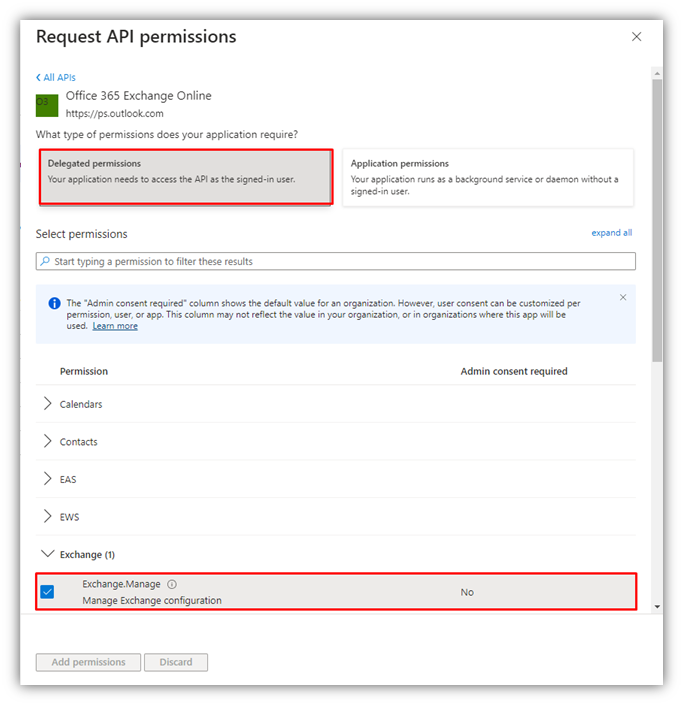
Add the delegated permission Exchange.Manage
Choose Add permissions box to finish.
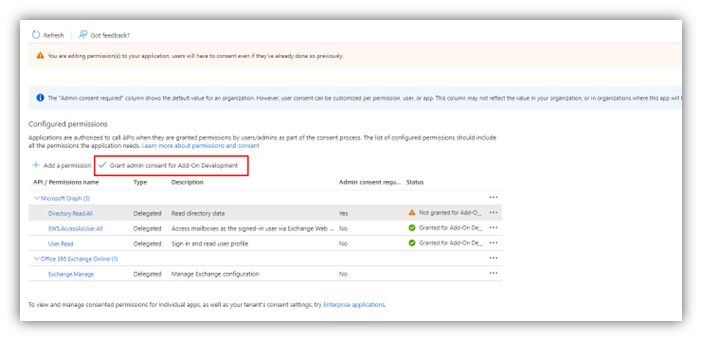
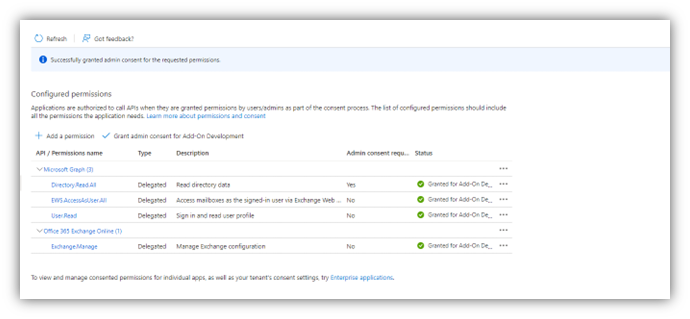
11. Finally you must grant admin consent...
so that you end up with this set of permissions:
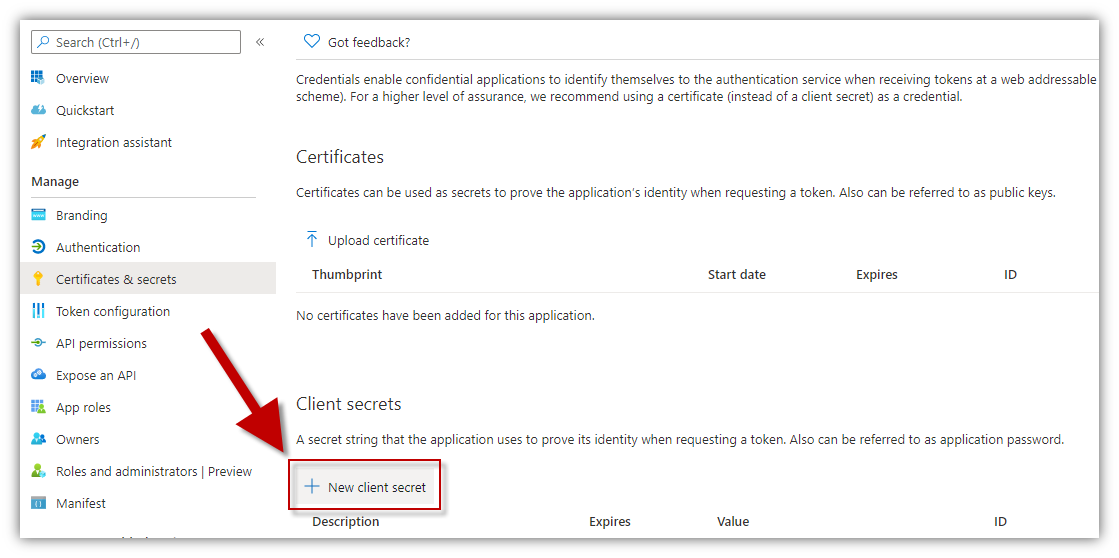
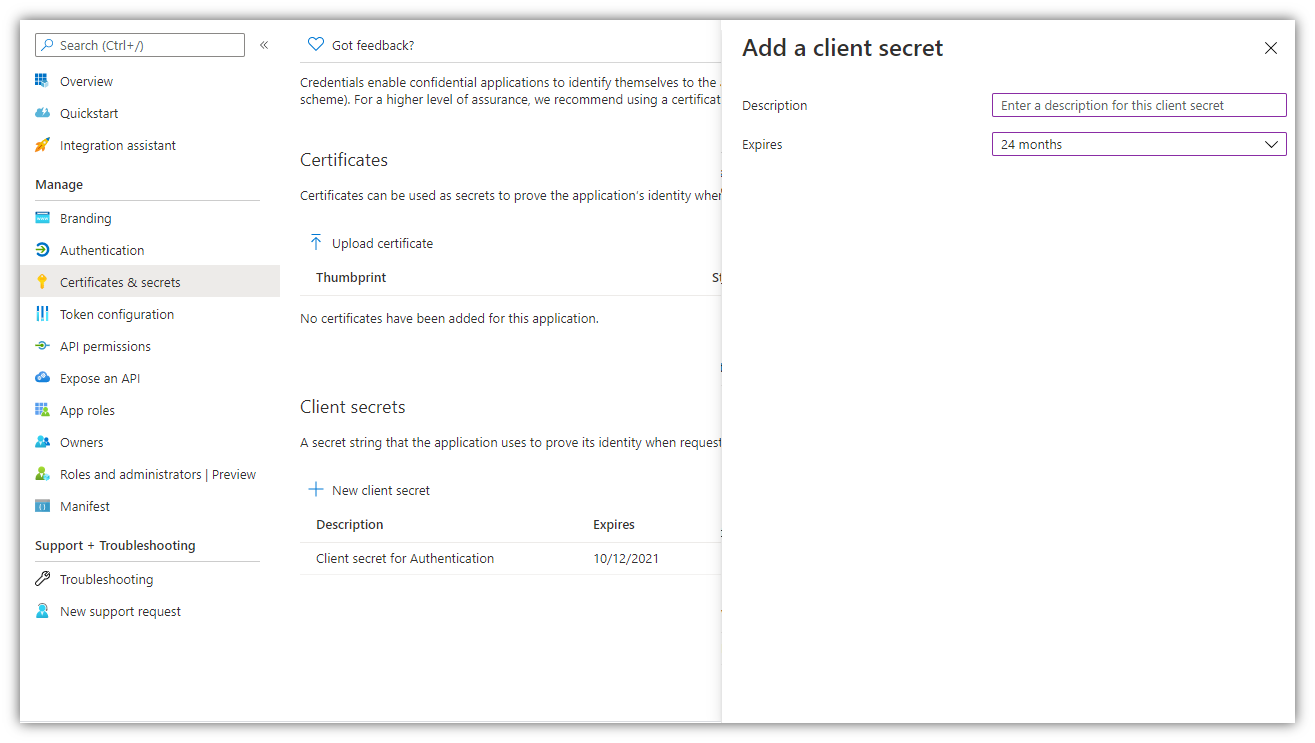
12. A Client Secret must be created.
Select 24 months (the longest expiry date):
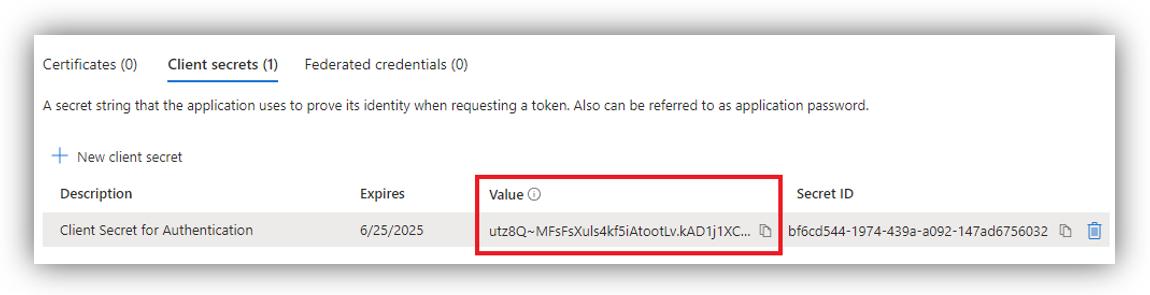
Click on the icon beside the key immediately to copy the value of the secret key to the clipboard as it cannot be retrieved later.
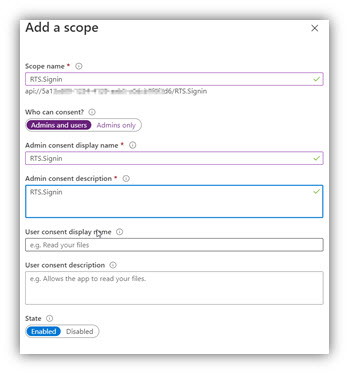
13. An API scope must be exposed.
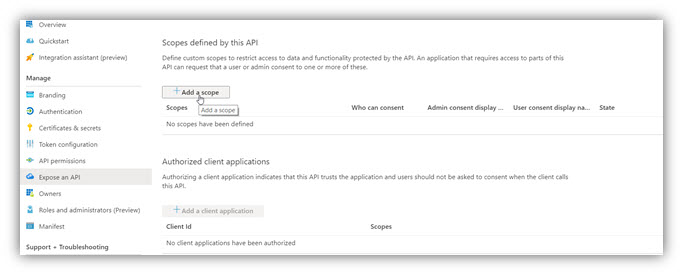
Next fill in fields as follows:
Click Add scope to complete this task.
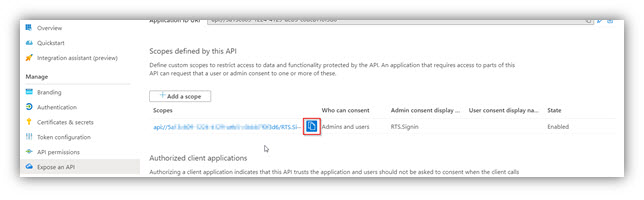
Now copy the Scope URI with the copy button as shown above, and save for RTS configuration.
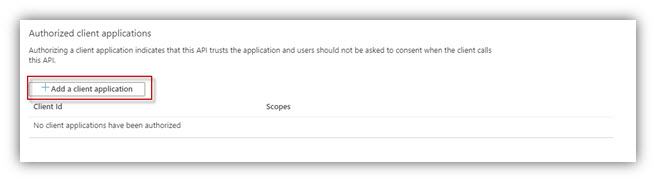
14. Add the application as an Authorized client application of itself.
Click [Add a client application]
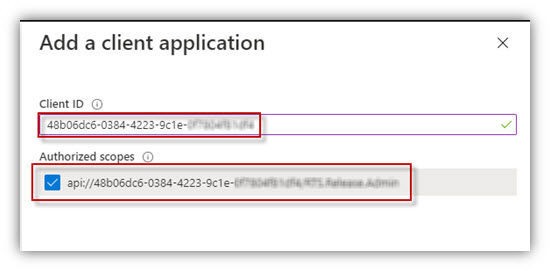
Fill the Client ID field with the Application ID of the app being configured
Click [Add application button] at the bottom of the panel.
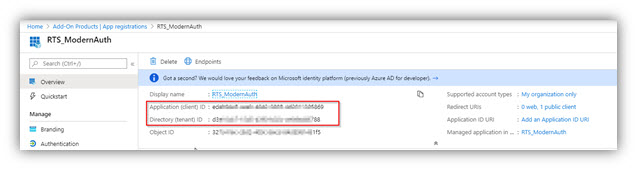
15. Note down the Application ID and Tenant ID for configuration of Realtime Service, along with the Secret key and the Scope URI.
Properties
Applies to: RTS 6.6+
Reference: TFS #239073
Knowledge base ID: 0290
Last updated: Jun 05, 2023
Tuan Dinh Cong
Comments